当前位置:
X-MOL 学术
›
Int. J. Commun. Syst.
›
论文详情
Our official English website, www.x-mol.net, welcomes your feedback! (Note: you will need to create a separate account there.)
Capitulation of mitigation techniques of packet drop attacks in MANET to foreground nuances and ascertain trends
International Journal of Communication Systems ( IF 2.1 ) Pub Date : 2021-04-20 , DOI: 10.1002/dac.4822 Sandeep Singh 1 , Anshu Bhasin 2 , Anshul Kalia 1
International Journal of Communication Systems ( IF 2.1 ) Pub Date : 2021-04-20 , DOI: 10.1002/dac.4822 Sandeep Singh 1 , Anshu Bhasin 2 , Anshul Kalia 1
Affiliation
|
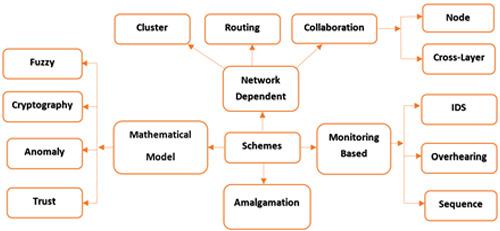
MANET is a kind of wireless ad hoc networks, in which mobile nodes operate in dynamic, distributed, and cooperative environment. Open nature of MANET makes it vulnerable to various kinds of attacks. Of these, the most severe are the packet drop attacks such as Blackhole attack, Cooperative Blackhole, and Grayhole attacks. The malicious nodes drop the packets as these packets are routed through them in accordance with the malefic strategy of the particular packet drop attack, which adversely affects the network performance. A substantial amount of research papers focus on dealing with packet drop attacks in the last few years, but security is still an impending issue. In this paper, we have presented the systematic review of the literature of last 6 years on all variants of packet drop attacks. We have classified these techniques into four categories, namely, mathematical based, monitoring based, network dependent, and amalgamation based which are further sub divided into 12 categories. These papers are categorized in a well-defined structure to bring out their contribution, to underline the left-out things, and to foreground the emerging issues for future research. Detailed observations are recorded following a panoptic study in order to identify and divulge more eligible and effective mitigation techniques in a particular environment.
中文翻译:

MANET 中丢包攻击的缓解技术的投降,以预测细微差别并确定趋势
MANET 是一种无线自组网,其中移动节点在动态、分布式和协作环境中运行。MANET 的开放性使其容易受到各种攻击。其中,最为严重的是丢包攻击,如黑洞攻击、协作黑洞和灰洞攻击。当这些数据包根据特定数据包丢弃攻击的恶意策略路由通过它们时,恶意节点丢弃数据包,这对网络性能产生不利影响。近年来,大量研究论文集中在处理丢包攻击,但安全性仍然是一个迫在眉睫的问题。在本文中,我们对过去 6 年有关丢包攻击的所有变体的文献进行了系统回顾。我们将这些技术分为四类,即基于数学的、基于监控的、基于网络的和基于合并的,它们进一步细分为 12 类。这些论文按定义明确的结构分类,以展示他们的贡献,强调遗漏的事情,并为未来的研究突出新出现的问题。在全景研究之后记录详细的观察结果,以便在特定环境中识别和披露更符合条件和更有效的缓解技术。并提出未来研究的新问题。在全景研究之后记录详细的观察结果,以便在特定环境中识别和披露更符合条件和更有效的缓解技术。并提出未来研究的新问题。在全景研究之后记录详细的观察结果,以便在特定环境中识别和披露更符合条件和更有效的缓解技术。
更新日期:2021-06-03
中文翻译:

MANET 中丢包攻击的缓解技术的投降,以预测细微差别并确定趋势
MANET 是一种无线自组网,其中移动节点在动态、分布式和协作环境中运行。MANET 的开放性使其容易受到各种攻击。其中,最为严重的是丢包攻击,如黑洞攻击、协作黑洞和灰洞攻击。当这些数据包根据特定数据包丢弃攻击的恶意策略路由通过它们时,恶意节点丢弃数据包,这对网络性能产生不利影响。近年来,大量研究论文集中在处理丢包攻击,但安全性仍然是一个迫在眉睫的问题。在本文中,我们对过去 6 年有关丢包攻击的所有变体的文献进行了系统回顾。我们将这些技术分为四类,即基于数学的、基于监控的、基于网络的和基于合并的,它们进一步细分为 12 类。这些论文按定义明确的结构分类,以展示他们的贡献,强调遗漏的事情,并为未来的研究突出新出现的问题。在全景研究之后记录详细的观察结果,以便在特定环境中识别和披露更符合条件和更有效的缓解技术。并提出未来研究的新问题。在全景研究之后记录详细的观察结果,以便在特定环境中识别和披露更符合条件和更有效的缓解技术。并提出未来研究的新问题。在全景研究之后记录详细的观察结果,以便在特定环境中识别和披露更符合条件和更有效的缓解技术。



























 京公网安备 11010802027423号
京公网安备 11010802027423号