当前位置:
X-MOL 学术
›
Int. J. Netw. Manag.
›
论文详情
Our official English website, www.x-mol.net, welcomes your feedback! (Note: you will need to create a separate account there.)
Industrial control protocols in the Internet core: Dismantling operational practices
International Journal of Network Management ( IF 1.5 ) Pub Date : 2021-04-07 , DOI: 10.1002/nem.2158 Marcin Nawrocki 1 , Thomas C. Schmidt 2 , Matthias Wählisch 1
International Journal of Network Management ( IF 1.5 ) Pub Date : 2021-04-07 , DOI: 10.1002/nem.2158 Marcin Nawrocki 1 , Thomas C. Schmidt 2 , Matthias Wählisch 1
Affiliation
|
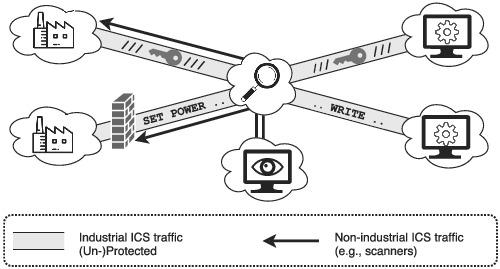
Industrial control systems (ICS) are managed remotely with the help of dedicated protocols that were originally designed to work in walled gardens. Many of these protocols have been adapted to Internet transport and support wide-area communication. ICS now exchange insecure traffic on an inter-domain level, putting at risk not only common critical infrastructure but also the Internet ecosystem (e.g., by DRDoS attacks). In this paper, we measure and analyze inter-domain ICS traffic at two central Internet vantage points, an IXP and an ISP. These traffic observations are correlated with data from honeypots and Internet-wide scans to separate industrial from non-industrial ICS traffic. We uncover mainly unprotected inter-domain ICS traffic and provide an in-depth view on Internet-wide ICS communication. Our results can be used (i) to create precise filters for potentially harmful non-industrial ICS traffic and (ii) to detect ICS sending unprotected inter-domain ICS traffic, being vulnerable to eavesdropping and traffic manipulation attacks. Additionally, we survey recent security extensions of ICS protocols, of which we find very little deployment. We estimate an upper bound of the deployment status for ICS security protocols in the Internet core.
中文翻译:

互联网核心中的工业控制协议:拆解运营实践
工业控制系统 (ICS) 借助最初设计用于围墙花园的专用协议进行远程管理。许多这些协议已经适应互联网传输并支持广域通信。ICS 现在在域间级别交换不安全的流量,不仅危及公共关键基础设施,而且危及互联网生态系统(例如,通过 DRDoS 攻击)。在本文中,我们测量和分析了两个中央互联网有利位置(IXP 和 ISP)的域间 ICS 流量。这些流量观察与来自蜜罐和互联网范围扫描的数据相关,以区分工业和非工业 ICS 流量。我们发现主要是未受保护的域间 ICS 流量,并提供有关 Internet 范围内 ICS 通信的深入视图。我们的结果可用于 (i) 为潜在有害的非工业 ICS 流量创建精确过滤器,以及 (ii) 检测 ICS 发送不受保护的域间 ICS 流量,容易受到窃听和流量操纵攻击。此外,我们调查了 ICS 协议的最新安全扩展,我们发现其中很少部署。我们估计了 ICS 安全协议在 Internet 核心中的部署状态的上限。
更新日期:2021-04-07
中文翻译:

互联网核心中的工业控制协议:拆解运营实践
工业控制系统 (ICS) 借助最初设计用于围墙花园的专用协议进行远程管理。许多这些协议已经适应互联网传输并支持广域通信。ICS 现在在域间级别交换不安全的流量,不仅危及公共关键基础设施,而且危及互联网生态系统(例如,通过 DRDoS 攻击)。在本文中,我们测量和分析了两个中央互联网有利位置(IXP 和 ISP)的域间 ICS 流量。这些流量观察与来自蜜罐和互联网范围扫描的数据相关,以区分工业和非工业 ICS 流量。我们发现主要是未受保护的域间 ICS 流量,并提供有关 Internet 范围内 ICS 通信的深入视图。我们的结果可用于 (i) 为潜在有害的非工业 ICS 流量创建精确过滤器,以及 (ii) 检测 ICS 发送不受保护的域间 ICS 流量,容易受到窃听和流量操纵攻击。此外,我们调查了 ICS 协议的最新安全扩展,我们发现其中很少部署。我们估计了 ICS 安全协议在 Internet 核心中的部署状态的上限。



























 京公网安备 11010802027423号
京公网安备 11010802027423号