当前位置:
X-MOL 学术
›
Comput. Secur.
›
论文详情
Our official English website, www.x-mol.net, welcomes your feedback! (Note: you will need to create a separate account there.)
Towards Multiple-Mix-Attack Detection via Consensus-based Trust Management in IoT Networks
Computers & Security ( IF 5.6 ) Pub Date : 2020-09-01 , DOI: 10.1016/j.cose.2020.101898 Zuchao Ma , Liang Liu , Weizhi Meng
Computers & Security ( IF 5.6 ) Pub Date : 2020-09-01 , DOI: 10.1016/j.cose.2020.101898 Zuchao Ma , Liang Liu , Weizhi Meng
|
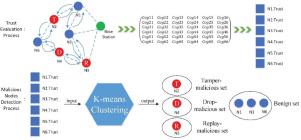
Abstract With the rapid development of Internet of Things (IoT), various smart devices can work collaboratively and construct a kind of multihop IoT network. However, due to the distributed nature, how to defend such kind of network against insider attacks remains a challenge, especially under multiple-mix-attack model where attackers can launch several attacks simultaneously. In this work, we consider a type of multiple-mix-attack that combines three typical attacks - tamper attack, drop attack and replay attack with an uncertain probability. For detection, we propose an approach called Distributed Consensus based Trust Model (DCONST), which can evaluate the trustworthiness of IoT nodes by sharing certain information called cognition. In particular, DCONST can detect malicious nodes and analyze their concrete attack behaviours via the K-Means clustering method. To further discuss the impact of cognition aggregation on detection accuracy and the additional burden on the network, we design three modes of DCONST: DCONST-Light, DCONST-Normal and DCONST-Proactive. In the evaluation, as compared with the similar methods of Hard Detection (HD) and Perceptron Detection with Enhancement (PDE), it is found that DCONST can achieve a better detection rate in the range from around 10% to 40%. In addition, DCONST-Normal and DCONST-Proactive can further improve the detection rate by 5% to 20% as compared to DCONST-Light.
中文翻译:

通过物联网网络中基于共识的信任管理实现多重混合攻击检测
摘要 随着物联网(IoT)的快速发展,各种智能设备可以协同工作,构建一种多跳物联网网络。然而,由于其分布式特性,如何防御此类网络免受内部攻击仍然是一个挑战,尤其是在攻击者可以同时发起多次攻击的多重混合攻击模型下。在这项工作中,我们考虑了一种多重混合攻击,它结合了三种典型的攻击——篡改攻击、丢弃攻击和不确定概率的重放攻击。对于检测,我们提出了一种称为基于分布式共识的信任模型(DCONST)的方法,它可以通过共享某些称为认知的信息来评估物联网节点的可信度。特别是,DCONST 可以通过 K-Means 聚类方法检测恶意节点并分析其具体攻击行为。为了进一步讨论认知聚合对检测精度的影响以及对网络的额外负担,我们设计了三种 DCONST 模式:DCONST-Light、DCONST-Normal 和 DCONST-Proactive。在评估中,与类似的硬检测(HD)和增强感知器检测(PDE)方法相比,发现DCONST可以在10%到40%左右的范围内实现更好的检测率。此外,DCONST-Normal 和 DCONST-Proactive 相比 DCONST-Light 可以进一步提高检测率 5% 到 20%。DCONST-Normal 和 DCONST-Proactive。在评估中,与类似的硬检测(HD)和增强感知器检测(PDE)方法相比,发现DCONST可以在10%到40%左右的范围内实现更好的检测率。此外,DCONST-Normal 和 DCONST-Proactive 相比 DCONST-Light 可以进一步提高检测率 5% 到 20%。DCONST-Normal 和 DCONST-Proactive。在评估中,与类似的硬检测(HD)和增强感知器检测(PDE)方法相比,发现DCONST可以在10%到40%左右的范围内实现更好的检测率。此外,DCONST-Normal 和 DCONST-Proactive 相比 DCONST-Light 可以进一步提高检测率 5% 到 20%。
更新日期:2020-09-01
中文翻译:

通过物联网网络中基于共识的信任管理实现多重混合攻击检测
摘要 随着物联网(IoT)的快速发展,各种智能设备可以协同工作,构建一种多跳物联网网络。然而,由于其分布式特性,如何防御此类网络免受内部攻击仍然是一个挑战,尤其是在攻击者可以同时发起多次攻击的多重混合攻击模型下。在这项工作中,我们考虑了一种多重混合攻击,它结合了三种典型的攻击——篡改攻击、丢弃攻击和不确定概率的重放攻击。对于检测,我们提出了一种称为基于分布式共识的信任模型(DCONST)的方法,它可以通过共享某些称为认知的信息来评估物联网节点的可信度。特别是,DCONST 可以通过 K-Means 聚类方法检测恶意节点并分析其具体攻击行为。为了进一步讨论认知聚合对检测精度的影响以及对网络的额外负担,我们设计了三种 DCONST 模式:DCONST-Light、DCONST-Normal 和 DCONST-Proactive。在评估中,与类似的硬检测(HD)和增强感知器检测(PDE)方法相比,发现DCONST可以在10%到40%左右的范围内实现更好的检测率。此外,DCONST-Normal 和 DCONST-Proactive 相比 DCONST-Light 可以进一步提高检测率 5% 到 20%。DCONST-Normal 和 DCONST-Proactive。在评估中,与类似的硬检测(HD)和增强感知器检测(PDE)方法相比,发现DCONST可以在10%到40%左右的范围内实现更好的检测率。此外,DCONST-Normal 和 DCONST-Proactive 相比 DCONST-Light 可以进一步提高检测率 5% 到 20%。DCONST-Normal 和 DCONST-Proactive。在评估中,与类似的硬检测(HD)和增强感知器检测(PDE)方法相比,发现DCONST可以在10%到40%左右的范围内实现更好的检测率。此外,DCONST-Normal 和 DCONST-Proactive 相比 DCONST-Light 可以进一步提高检测率 5% 到 20%。


























 京公网安备 11010802027423号
京公网安备 11010802027423号